Online testing
You may online test PlugSSO at https://elshaug.xyz having path /sso protected. There will be Single Sign-On between all realms in the same domain. For testing purpose, internal login accepts all usernames having password = password. If more than 4 incorrect login attempts, user will be banned for 1 hour. You may also test using misc sub paths under each realm.
Passkey/U2F prerequisite:
External USB or NFC security key is required, or running on a device having PIN or biometric security enabled like Fingerprint, Touch ID or Face ID
OTP prerequisite:
OTP Authenticator app is required e.g. installed on iPhone or Android (using an app from Microsoft, Google, Authy,…)
Logout: /plug/logout Note, you will also be logged out when going from one domain to another or closing browser
Domain1
Prelogin: Google, Azure and internal authentication
Authorization: No
Multi Factor: Selection (OTP, Passkey, Passkey user-less)
Comment: Multi Factor can be selected having OTP as default.
Selecting "Passkey user-less" will automatically start
username-less authentication (Prelogin not needed)
See also comments for Domain2/Domain3.
Realms for testing:
/sso/app1
/sso/app2
Domain2
Prelogin: Google, Azure and internal authentication
Authorization: No
Multi Factor: Passkey
Comment: Password is not needed, but username is required. Username
will be automatically given by the Prelogin authentication.
When using Microsoft or Google you may already have
the auth cookie and will not notice this authentication.
On first time use, you need to register your
Authenticator/ID. You may later on register as many as
you want e.g. when using another device or using
a different username.
Realms for testing:
/sso/app3
/sso/app4
Domain3
Prelogin: Only for registration - Google, Azure and internal authentication
Authorization: No
Multi Factor: Passkey user-less
Comment: Using user-less we do not have to provide any username
or password. Authenticator/ID needs to be registered on
first time use having a Prelogin and the traditional
authentication. You may later on register as many as you
want e.g. when using another device or want to use
a different username. When having several usernames
registered, you have to select one of then from the list
that pops up during the login process.
Realms for testing:
/sso/app5
/sso/app6
Domain4 Prelogin: No Prelogin, using direct Google authentication Authorization: No Multi Factor: No Realms for testing: /sso/app7 /sso/app8/abc
OpenID Connect authentication require a consent on first time use. This means user have to accept exchanging profile attributes like mail address with PlugSSO. Installing and using mobile apps you are probably familiar with this concept.
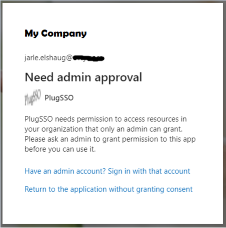
Microsoft login selection is configured with Azure authentication having AzureAdAndPersonalMicrosoftAccount. This means all users with a work, school, or personal Microsoft account are allowed for authentication.
Note, you may not use your work or school account unless your Azure tenant administrator have granted global consent permissions (default turned off) or specific consent have been defined in Azure for PlugSSO. So, you most likely have to use a personal Microsoft account (@outlook.com, @hotmail.com, @live.com, …). If you get a dialog box like shown in figure below, you have to click Have an admin account? Sign in with that account and then specify your personal account.